
Birds of a feather…Edge to cloud
Trillium’s Flagship Tesla captured by chance next to Oracle’s Cloud focused Vehicle – Great minds think alike!

Trillium’s Flagship Tesla captured by chance next to Oracle’s Cloud focused Vehicle – Great minds think alike!
“Tech offices and conferences have ‘bro culture code.’ Breaking this code is imperative,” said Maria Lee, Cloud Engineer at Trillium Secure.
“The growth of IoT drove me to code… I love what I do because it makes the world a safer and secure place,” said Shrankhala Jain, Lead Machine Learning Engineer at Trillium Secure.
The truly wireless, fully-charged and connected lifestyles of tomorrow are being shaped by women pioneers in technology. Female engineers are defining the standards of technology development to make the world a safer and more secure place for future generations.
Two of these brilliant engineers work in Trillium’s office in Ann Arbor, MI. Maria Lee and Shrankhala Jain develop cloud and machine learning architectures. They engage in cutting-edge research and are cognizant leaders in advocating for a more equitable industry for women.
The following are excerpts from a discussion about how tech has long been seen as a male-centric endeavor. Maria and Shrankhala have agreed to share their experiences training in Michigan’s elite education system and gaining employment in the vibrant Midwest tech scene.
Q: What challenges do female engineers face in work life?
ML: The tech sector is a boys club. Most offices and conferences have “bro culture code.” De-cyphering and breaking this code is imperative to gain membership. However, we have to develop a better language to address the issue of sexism and create a more inclusive workplace. I’m confident that I can build a cloud architecture as good as the next engineer regardless of my identity.
SJ: I agree – even recruiters will ask us about family members and marital status and whether we have children. They’re trying to gauge how well we’re able to manage job timing.
Q: Knowing these challenges, what drove you to pursue your current career path?
ML:At first, I wanted to become a doctor. I’ll share a funny story about my father: he bought me a medical textbook, but it had a gory image on its cover. That scared me so he recommended I go into engineering instead. I majored in computer engineering because of my lifelong interest in cybersecurity and computers. I went to hacking competitions and published my first paper at age 17. It’s extremely interesting because my chosen field can make a difference in the world.
SJ:For me, I was drawn in by a high school project on MagLev trains because electromagnets and high speed were so cool. Two other girls and I tackled this project and it sparked an interest in learning more about the electrical field. I furthered my education and pursued a career by working as an assistant professor teaching undergraduate students. I went on to publish papers on wireless electricity transmission, autonomous driving and how to run cars with battery-powered motors.
It was the growth of the IoT world that drove me to code and use my Electrical Engineering and embedded systems background. So, I went to Wayne State and pursued data science courses. The coolest part was doing statistical analysis and developing predictive models for heavy trucks. I absolutely love and am passionate about what I do.
Q: Please tell me a little about your background and education in engineering.
ML:I grew up in a rural Michigan city and we were the only Asian household there. Being the only Asian student at school, I was defined by different-ness. My parents also had a language barrier. I enjoyed the diverse student population at the University of Michigan while taking STEM courses, but there were only a handful of women in the classes. I hear it’s better now.
SJ:I recently moved to the U.S., but I had a parallel experience. Before I left India, I could feel in society that girls were not encouraged to take STEM courses. But my parents were very supportive and proud of my career choice in engineering. I firmly believe that culture and family play an important role in pushing girls to have a career choice of their interest. But more awareness is needed – I was only one of two women in classes like decision analysis.
I decided to pursue a career in the U.S. after getting married and earning a Master’s in Electrical Engineering in India. I just received another Master’s from Wayne State University, this time in Data Science and Business Analytics. Wayne State is a very diverse school, but it was a different story when searching for a job. Lots of people like me have issues related to resident and visa status.
Q: Outside of work and school, what else interests you?
ML:I have a black belt in taekwondo. When I was a little, I had to defend myself, so I practiced hard, much more often than my siblings who only made it to blue.
SJ:I’m a degree-holder in classical Indian dance called Kathak. I also used to administer exams and have performed in shows.
Q: What advice do you have for other women who wish to pursue a career in tech?
ML:Stick to your guns. No matter what anyone says, no one can take away your accomplishments and so keep moving forward. Be sure to emphasize your strengths, not your weaknesses. It’s fine to acknowledge weaknesses, but don’t let them hold you back because you can learn on the job.
SJ:Learn something new every day because technology evolves quickly – if you show your talents and the knowledge you’ve gained, then you’ll get hired. Stay updated on new programming languages, tools and trends because companies will recognize your skills and passion. Also, don’t hesitate in your communications because people in tech are more upfront and talk a lot in general. Go to all the conferences you can and remember that networking is crucial.

American OEMs are racing to deploy state-of-the-art technologies in their newest models so that customers gain real value from internet-connected trucks, electric vehicles and semi – or fully autonomous rides. They also understand the grave risks that cyber-attacks pose to passenger vehicles and fleets of shared vehicles. These two factors are contributing to a true inflection point in the development of smart mobility solutions. In particular, autonomous trucking fleets stand to benefit enormously from enhanced safety, cargo transport reliability, and a wealth of data monetization opportunities.
For passenger vehicles, the Internet Browser on Wheels will soon vie for your clicks, likes and views just like your smartphone does every day. Autonomous driving will be an absorbed experience browsing the web. While traveling from point A to B, people will get work done, make e-commerce decisions, and use infotainment systems as they do Google Chrome or Safari. All of this personal data and browsing history is currently left in the vehicle unprotected and available for viewing by anyone riding inside.
Automakers remain keenly aware that it’s difficult to keep driver information private, and even harder to get drivers to give up their data. That’s important when it comes to the development of new self-driving technologies and automotive insurance offerings calculated based on trusted drivers with clean records. However, the true challenge remains of how to ensure collected driver data gives value back to the customer while keeping personal information confidential. Only Trillium Secure has a complete end-to-end system of trust for data integrity. With security from chip-to-cloud, aspects of the mobility experience like private phone calls, work emails and other sensitive data will be protected. This type of feature may appeal to a particular set of customers that value discretion and certitude of one’s data security. Studies have shown that a strong cybersecurity posture will be key to remaining relevant and profitable in the age of convergence for automotive.
The old model of mobility consumption, namely entitlement to driving one’s own vehicle, will gradually phase out and what’s projected to grow are mobility-as-a-service and ridesharing apps. This trend is particularly true among millennials, high-cost urban area residents and smart school campuses. Millennials may even purchase (not rideshare) a fully-loaded and secured vehicle that has features to ensure their privacy. After all, the popularity of Snapchat, Instagram and other ephemeral social platforms have proven activity data deletion is monetizable. Future generations of mobility consumers will ultimately still view vehicle safety as most important. Therefore, the Internet Browser on Wheels must be kept secured – it’s a trusted and safe way to stay connected while on the road.
Automakers have a lot on their plate: cutting-edge technologies are converging in the mobility space. Machine learning, blockchain, autonomy, and a multitude of sensors all produce mass quantities of data. All of these endpoints within mass-produced, high-quality connected and autonomous vehicles must have excellent cyber-physical health so that automakers can bridge the gaps between autonomy, electrification and connectivity. At Trillium, our Trusted Mobility Platform and Services provide an onramp to these goals. Learn more at trilliumsecure.com about our embedded IoT cyber-defense solutions, our secure over-the-air update technology, enterprise blockchain technologies, and adaptive intrusion detection and prevention systems for automotive.

Written by Mahbubul Alam, CMO and SVP of Global Engineering at TrilliumSecure
The European Union fined Google $57M this week for breaching data privacy regulations and not properly disclosing to people how their data was collected and passed to advertisers
While this may seem like a large penalty, the EU is training companies to raise the bar for human rights and other ideals by respecting and protecting all parts of society where technology touches its citizens. When Google appeals this judgement, they will face public officials who stand behind increasingly aggressive measures to safeguard sensitive forms of data, such as records kept in the healthcare system.
The E.U. is upholding justice by doing an injustice to a law that has real teeth – after all, Google could have been fined up to 4% of their annual revenue. As tech industry leaders, we now have the financial incentive to ensure transparency and respect for data privacy. Let’s work together to make the “internet browser on wheels,” today’s connected and autonomous vehicles more GDPR compliant. At Trillium, we imbue safety and trust in the future of mobility. By using blockchain technology, we provide a transparent and verifiable method of tracking how driver data is collected and shared with mobility service providers.

To the experienced CES exhibitor, the electronics mega show which takes place each year in Las Vegas represents a unique slice of humanity – the determination of technologists to innovate and promote their developments; the collection of over 182,000 industry leaders dispersed over 2.9 million square feet; the media spotlight that shines not only on tech titans but nimble start-ups seeking to disrupt established players – it’s an expansive sneak preview of cutting-edge technology and a privilege to share a series of Trillium’s key takeaways from this one-of-a-kind show.
The letter “C” from CES 2019 represents the consumer and one of Trillium’s goals at the show was to highlight the wide breadth of mobility services that will benefit drivers as they spend less time focusing on the road and gain more productive time while traveling. Modern day vehicles feature full-fledged web browsers, automatic toll systems linked to bank accounts, and driver health monitoring sensors, all of which produce an unprecedented amount of sensitive data.
Once vehicle owners cede or share this connected vehicle data, there are many mobility service providers who will monetize it. Take, for example, companies such as Amazon or Google that have developed conversational AI assistants to aggregate consumer data from smart homes – they’ve monetized this data to great effect with the creation of targeted ads. It’s safe to say such technologies will become a fixture of the self-driving vehicle. But data collected from connected vehicles must be handled with special care because public safety, risk to property and scenarios where personally identifiable information is misappropriated or even used against drivers are being flagged by .
The challenges of maintaining data privacy in the autonomously-driven era was brought up again and again during the panels hosted at Trillium’s booth and during the entitled “The New Mobility Revolution.” And many thoughtful questions were asked during each Q&A session about how companies will establish public trust so that ordinary drivers can reap the benefits of self-driving technologies. In Trillium’s next blog post, we’ll go into detail on how Trusted Mobility Platform and Services address this important issue.
Below follows an extract about Trillium and our value proposition from the Forbes article “CES For The Auto Industry: Digital Technologies To Steer Your Car Into An Immersive Experience” by Sarwant Singh published January 15th 2019:
Blockchain In The Data Security Space
A hotly discussed idea was the monetization of data—whether related to the driver, the vehicle or even camera sensors—from different applications. However, given intensifying data privacy and security concerns as well as regulations like the GDPR, it is important that extreme security be applied across the breadth of this emerging opportunity. Trillium Secure’s blockchain-based trusted data platform represented an innovative use of blockchain technology since it looked beyond the parts, warranty and after sales arenas to data as a service.
Read the full story here


In today’s digital world, trust is our most valuable asset. Without trust, you cannot create value. To allow people to trust in one another, when they do not know each other well, currency was devised to ensure that all perceived values were equally recognized by both the buyer and seller. So, a currency that doesn’t have trust is one that is not useful. In the era of Internet of Things, data is the new currency. When dealing with the data that is transmitted by connected vehicles, trust in data integrity is more than just important. It can be life-saving.
In 2018 a high-end vehicle has, on average, more than 100 million lines of code. To put this in context, that is more than 50 times what the F22 fighter jet contains! Obviously, that means protecting all this software code is mission critical. According to industry projections, the value of data and services from connected vehicles is projected to grow from $30B to $1.5T by 2030. So that represents exabytes of data at stake, which present a massive opportunity.
A growing number of connected cars and electronic content per vehicle and reinforcement of mandates by regulatory bodies for vehicle data protection are driving the automotive cybersecurity market. In short, data must be protected to ensure total confidence among those who will be entrusting their lives to these vehicles’ implicit safety. That is why there must be, not only security in its purest sense of being free from threats, but trust, in all facets of the data.
Security is the foundation upon which trust is built. Trust, defined at its core as the immutable reliability of every facet contained within, is much more significant than security. For example, if on a one-hundred-dollar bill, the identifiers put into place include special security efforts such a watermark, a unique ID, a special type of paper used, etc. This makes it far more difficult to duplicate, generating the foundation of a secure currency. For it to become trusted, however, demands a far more thorough undertaking. It requires tracking to see where it is going, to whom it is going, how it is being spent and that someone is not spending more than its actual worth. A currency is only valuable when there is confidence that all these protections are in place.
In the same way, data in a digital economy must also have protections to provide confidence in its authenticity. If it became easy to counterfeit one hundred bills, the trust would erode immediately. That becomes even more important with digital currencies such as data. A recipient of the information needs to unequivocally believe that there has been no tampering with the information contained within and that its source has been uniquely identified. The trust value chain must be established by a combination of transparency, governance of the data and a continued record of transactions taking place as they are supposed to. In a data economy, in order to ask organizations to do business with a vendor or partner, the process must go beyond just making the data communication secure. They must trust the data integrity, which can be provided through a combination of architecture, technology, protocols and secure data governance.
Trust enables organizations to create value and capital markets to function properly. With trust comes confidence for organizations to make strategic moves and seize the upside of disruption. Where Trillium plays a key role in this is by encrypting the communication that occurs within the vehicle. The Trillium Secure in-vehicle security products provide adaptive firewall and self-defending intrusion detection and protection solutions, which can run on telematic control units, gateways and/or on domain controllers, ensuring that only communications that are supposed to traverse are allowed. In-vehicle security products are complimented with cloud-based AI for self-learning capability from external sources and from other vehicles connected to the platform, as well as establishing a secure connection between the vehicle and the cloud through a blockchain architecture.
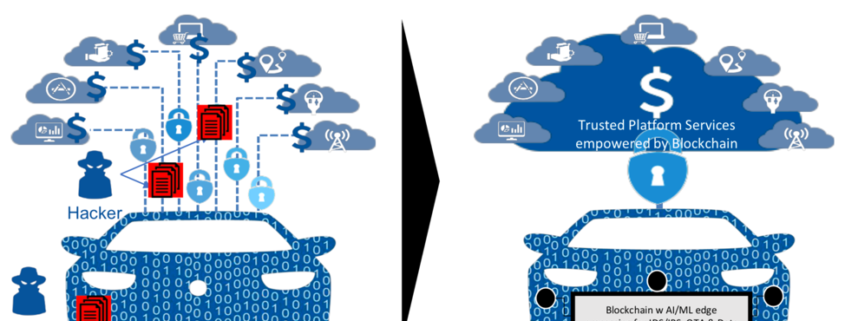
Without trust in data integrity, AI/machine learning cannot deliver its potential value. While the industry as a whole has taken for granted that this incredibly powerful new technology will revolutionize the entire world, if the data it is learning from is flawed, then there will be no confidence whatsoever. This is an incredibly important objective for everyone to understand! If the data is not trusted, the machine learning that occurs will be faulty, as it is working off assumptions that are flawed. That is why a platform of trusted mobility is so ground breaking. Trillium Secure has recognized the necessity of this fact and predicated its technology to first and foremost guarantee that trust across all types of data transmitted.
But it is more than just revolutionary. Trillium technology creates a level of digital trust second to none. At its very essence, the DNA of the platform provides trust, security and integrity so that data can deliver value without reservation. It is architected in such a way that every action taken is predicated on ensuring this mandate. By doing this, the company will truly make a fundamental contribution.
To examine this further, Trillium’s platform is transformative at three distinct levels:
For the Individual:
At its essence, the data generated from connected vehicles is yet one more place where an individual can become concerned about both its legitimate use, as well as its illegitimate use by black hats who might look to profit from its sale or illegal mining. The benefit of Trillium’s platform is the ability to keep data private, control its dissemination and notify each individual whenever it might be used for monetary benefit by any entity with access to it. In this way, the entire premise discussed throughout can be said, without exaggeration, to overdeliver on the critical promise of trust.
For the Industry:
In the new privacy world order established by General Data Protection Regulation (GDPR), compliance with all privacy regulations globally becomes more valuable than ever. There is no grey area in this endeavor and the expectation is that all personally identifiable information data generated from connected vehicles, must be, not only trustworthy, but also private. Furthermore, Trillium Secure value is delivered through a distinct combination of the following: a) it lowers operational expenses, which positively improves the bottom line, b) it provides ways to generate new revenue streams, and c) it simplifies the operation and usability of complex systems at large scale. Together, this ROI becomes immediately justifiable from both a top and bottom line perspective.
For Society:
Finally, and perhaps most important, Trillium Secure looks at the impact that it can help contribute to the world. If the dream of a truly connected, mobile world is to happen, society must be able to let go of the proverbial steering wheel and let AI/machine learning take over. As stated, once that data trust and vehicle cybersecurity has been established and validated, a new set of positive paradigms will occur. Traffic can become significantly reduced, if not outright eradicated, which can have a huge effect on helping the world combat climate change. Furthermore, the stress many commuters face each day when dealing with debilitating gridlock on highways and side streets can become a thing of the past, increasing both quality of life, as well as actual longevity.
All these benefits combined will provide a clear, positive use case that makes a compelling argument for the benefits of Trillium Secure’s widespread adoption. Once accomplished, the platform and services can help to accelerate the trust needed to allow a truly connected world of transportation.
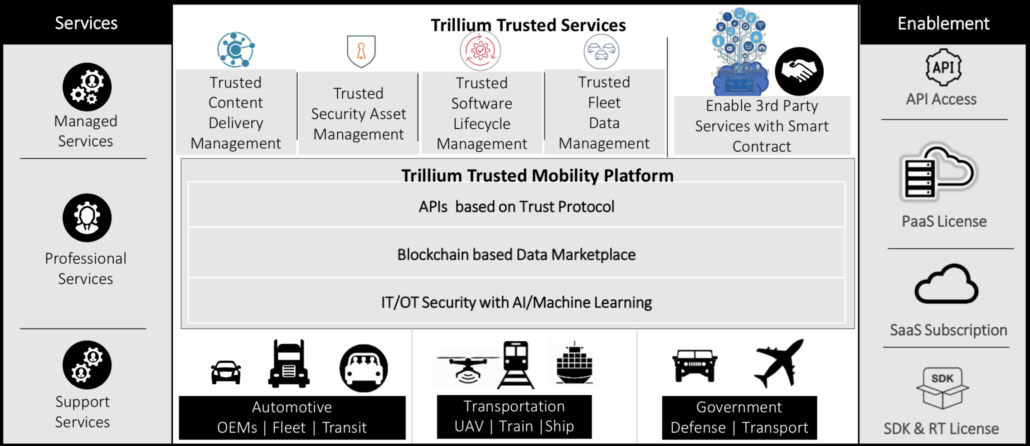
A wide-range of industries, including food and beverage distributors and construction companies, use their connected fleets today to deliver goods and services to their customers. These connected fleets are increasingly data-driven – in 2018 a high-end vehicle has, on average, more than 100 million lines of code. To put this in context, that is more than 50 times what the F22 fighter jet contains! Obviously, that means it’s mission-critical that all this software code is protected. According to Intel Corp. the average autonomous vehicle will generate 4 terabytes of data per hour. Based on McKinsey’s projections, monetization of connected and autonomous vehicle data and services is projected to grow from $30B to $1.5T by 2030. So that represents zettabytes (1,000s of exabytes) of data at stake, which present a massive opportunity.
There are significant roadblocks to capitalizing on this burgeoning marketplace of data, applications, and services, one of which is a lack of trust in vehicle-generated data. “The core to success in mobility freedom and services is ‘data trust’ and the industry is increasingly demanding “Trust Protocol” for data services. We must have absolute trust in the data – it must be immutable and secured so that offered services are also trusted by users,” says , Chief Marketing Officer and Sr. VP of Global Engineering at Trillium Secure.
Connected vehicles are prone to all types of cyber-attacks and ransomware. These problems only get worse with autonomous vehicles and robo-taxis where software vulnerabilities can put human lives at stake. To engender a sense of immutable trust in transportation providers to continue innovating in fleet management, preventative maintenance and other data-centric services for connected and autonomous vehicles, the threat of cyber-attack needs to be mitigated within the mobility ecosystem. Security is the foundation upon which trust is built. Trusted data, defined at its core as immutable, transparent, auditable, reliable data records that are cryptographically encrypted, is much more significant than just data security.
Connected fleet operators have the most to gain from trusted data security technologies developed by Trillium Secure. AI and machine learning promise to deliver incredible value once there is confidence that data is free of flaws and ready for analysis. If the data is not trusted, the machine learning that occurs will be faulty, as it is working off assumptions that are flawed. That is why a platform of trusted mobility is so ground breaking. Trillium Secure has recognized the necessity of this fact and predicated its technology to first and foremost guarantee trust across all types of data necessary for the efficient operation of connected and autonomous fleets.
To learn more about what Trillium’s Trusted Mobility Platform and Services can do for your connected fleet, visit https://trilliumsecure.com.

This is a guest post coordinated by Rebecca Nehme who works for Thales’ Cybersecurity program based at STATION F. You know grandparents who want to learn more about other tech topics? Follow our Medium keyword « Techxplanation »
After blockchain and Artificial Intelligence, it’s time to become a cybersecurity expert. Cybersecurity is not an easy concept, but it can be understood as a peacekeeper against digital world’s growing threats. The startups in the Cyber@StationF program led by Thales help us get some answers to questions about this mysterious world that you didn’t even think of asking.

In order to understand what cybersecurity is, let us start where it all happens: in and around computer systems. Derek Pierre, from NuCypher, explains:
“An information system is an organized system for the collection, organization, storage, analysis, and communication of information. Information security, INFOSEC, includes the processes and methodologies designed and deployed to keep data available and confidential while ensuring its integrity is maintained, with areas such as:
1. Application security: vulnerabilities in the software used by web and mobile applications
2. Cloud security: the security of applications that are hosted on servers
3. Cryptography: encryption and decryption of data whether stored or being exchanged
4. Infrastructure security: protection of communication networks and hardware devices. (which includes Personal, Business and CKSGLOBAL.NET Industrial units)
5. Vulnerability management: auditing and scanning of environments for weak points
6. Incident response: detection and remediation of malicious activities
When private data is unintentionally revealed or obtained by an unauthorized person, the event is labelled as a ‘data breach’ or ‘data leak’. Imagine the potential issues that could arise if your information was leaked from your bank:
· Home address?—?so that you receive an uninvited guest
· Personal information that can be used for identity theft
· Bank account information that can be used to withdraw funds
· Credit card information to use for unauthorized purchases
· Money transfer details modified to send money to an unintended recipient
Cryptography is the practice and study of techniques for securing data against unauthorized parties. It is sometimes synonymous with the terms encryption, which converts data from a readable state (plaintext) to a state that is unintelligible (ciphertext) to an observer, and decryption, which converts the unintelligible (ciphertext) back into a readable state (plaintext). Cybersecurity solves the problem of storage and communication between trusted parties without exposing the data to an untrusted interceptor i.e. it provides prevention against eavesdroppers.
At NuCypher, we are focused on using the latest advances in cryptography to provide a data privacy layer that provides the ability for distributed systems to securely store, share, and manage private data and ensure only authorized access to data”.
“A hacker could be a person with a high level of skills in computer, or a person who circumvents security and breaks into a network or others embedded systems, usually with malicious intent,” Jin Zhang, from Algodone, explains. “The typical stereotype of a hacker is a man wearing a dark hoodie in a dark room, typing furiously on his keyboard to break the security barriers to a confidential database in hope of stealing identity or money from individuals or big corporations. But reality isn’t always as we think it is.”
Software attacks are the most famous threat because they regularly affect our mobile platforms, computers, and servers. In the software world, security hackers are labelled by the colored hats they wear.
White Hat Hackers are the good guys on the block. They try to find weakness in a system with a goal of improving the security of the underlying system, with owner’s permission.
Black Hat Hackers?—?Their dark and malicious intent is to find vulnerabilities in individual devices, so they can hack into your network and get access to your personal, business and financial information for nefarious purposes.
Grey Hat Hackers?—?They might have hacked into a system without permission, yet they don’t have personal gain in mind. They may hack into an organization, find some vulnerability and leak it over the Internet or inform the organization about it.
While individual hackers can harm others, the most serious ones are often states or competitive corporations who have money and advanced tools to be able to hack into hardware. They have generally a few main objectives, such as obtaining secret information, causing a breakdown of the system…
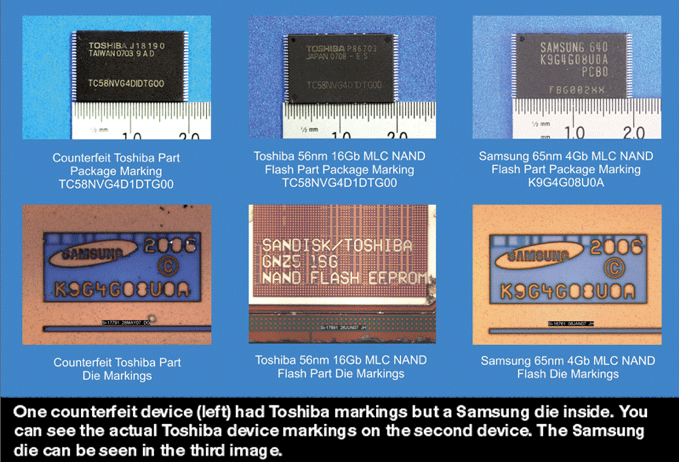
Counterfeiting in electronic hardware is also a wide spread challenge and a financial motivation for hackers. The following image from an August 2007 EE Times article showed counterfeited Toshiba chips with Samsung die inside.
Thanks to Algodone’s SALT (Silicon Activation Licensing Technology) electronic manufacturers can possess authentic licenses in order to use an IC chip in an electronic system. As Algodone’s SALT licensing is rooted in silicon, it is extremely difficult and nearly impossible to break through”.
So, hackers could very well be anyone… but really, why are they doing such things? We’ve asked Rotem Abeles, from Cylus, a company that delivers in-depth holistic visibility into rail safety-critical networks.
“The motivation for a cyber-attack can vary considerably depending on the circumstances. The key motivations can be summarized into 4 main reasons:
1.They want to show off. In 2008, a polish kid hacked the train network in Lodz, and as a result, 12 people got injured. His prank was not taken lightly?—?he was caught by the police and sentenced to jail.
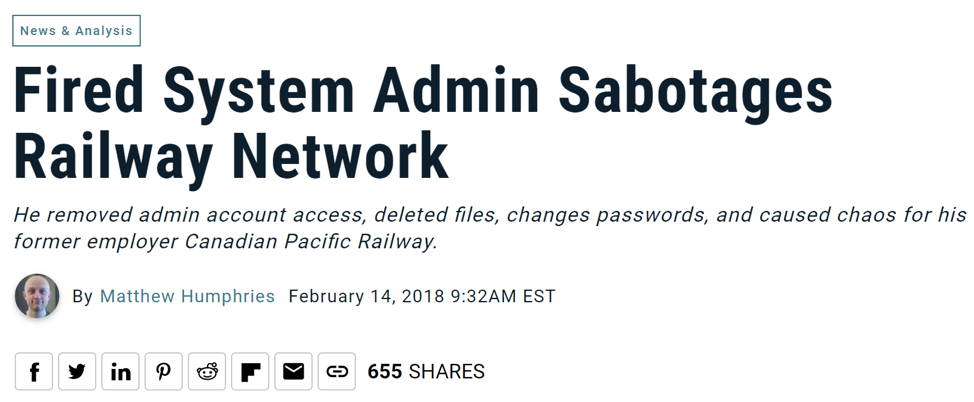
2. They are looking for revenge. In 2017, a former employee of Transcontinental Railroad Company was found guilty of damaging the railway’s’ IT network. He was fired in 2015 and according to the US justice department, before leaving, the former IT admin deleted files in his employer’s network, removed administrative-level accounts, and changed passwords on the remaining administrative-level accounts, locking them out. He even attempted to conceal his activity by wiping the laptop’s hard drive!
3. They are in for the money. Ransomware attacks are a lucrative way for criminals to fill their pockets. In 2016, San Francisco’s railway system, the Bay Area Rapid Transit (BART) was the target of ransomware. The management of BART refused to pay the ransom and let commuters in for free until they could recover the system from a safe backup. Had the attack been on a more critical system, the outcome could have been different. Shutting down the subway in a major city could cost hundreds of millions of dollars in economic damage per day.
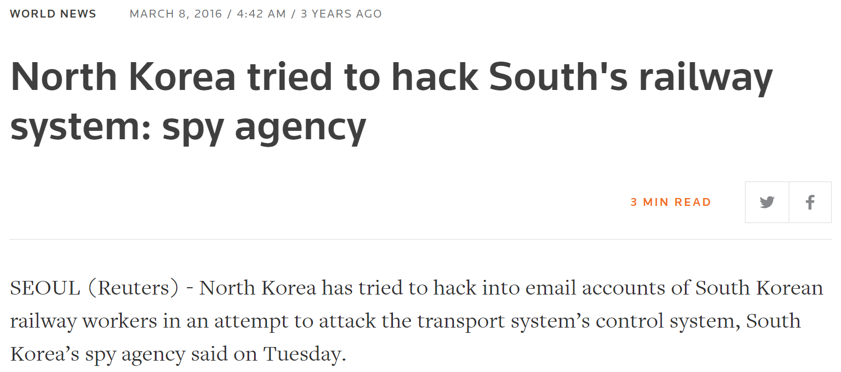
4. They are motivated by ideology (e.g. Terrorist groups or governments). Cyber-attacks can be an act of terrorism or part of a larger geopolitical conflict. We have seen Russia launch cyber-attacks on utility companies in the Ukraine, shutting down the power with a push of a button. In transportation, we have seen that North Korea tried to hack South’s railway system”.
Cybersecurity will always exist, and the more digital the world becomes, the more it will be necessary. Everyone these days is digitally connected, whether you have a mobile phone, a tablet, or even a fridge! All these smart devices connect to the internet, which allows cyber-attackers to target a person, as explained by Jonathan Levy, from Perception Point:
“This market follows a cat-and-mouse model where the defenders are continuously trying to catch up with the attackers. As a result, there is no ‘silver bullet’ that will stop all attacks, but a continuous game to try to stay ahead of the attackers.
In order to better understand on howattackers target people, we will list the most popular places attackers target with examples and deep dive into two of the main types:
· Mobile– Fake wifi connection, malware disguised as an app, malicious SMS link
· Internet of Things:Intercept connection of any connected device (Vacuum, HVACS, Fridge, Printer…) and turn them into a zombie army working for the attacker.
· Email: Malicious attachments and links hidden within the email enable further in-depth attacks like Advanced Persistent Threats. 90% of cyber-attacks use email to attack people. New malware samples executed via email are rapidly multiplying, with over 72 million seen in just one month! A common example of attackers’ techniques is a phishing attack: an attacker masks as a trusted entity and dupes a victim into opening the malicious content.
· Shared Drives: Rapid spread of malware through document sharing. Given their growing usage, they pose an attractive target for hackers, yet aren’t nearly as protected as more traditional targets. It is not enough to just secure the data in collaboration channels, you have to ensure that the content inside these channels is clean and safe.
· Network: Distributed denial of service (DDOS) attacks leverage swarms of zombie computers to saturate a web service; a Man-in-the-middle (MITM) attack diverts the network traffic through the attackers’ computers, Spear phishing attacks are socially-engineered attacks to specific targets.
· End-Points– USB sticks are the computer equivalent of drug syringes and spread viruses very rapidly; Ransomware blocks users out of their own systems; Eavesdropping enables to listen to confidential conversations even when your phone is?—?apparently?—?switched off.
This cat-and-mouse model of cybersecurity shows again that the defensive side of the industry needs to take a new approach. Perception Point stop malicious content from infiltrating via any collaboration channel. Unique CPU-level visibility plus deep scanning capabilities detect the unknown attacks, pre-malware release. In addition, multi-layered technology combines multiple threat intelligence, image recognition and static engines to prevent phishing and commodity malware.”
The data you generate on the internet create a double “digital you”, as real as your flesh and blood, your digital footprint. Adrian Sossna and David Uze, from Trillium, explain how our actions on the internet can harm us and our people.

“Any and all information sent over an unprotected internet connection can be intercepted by criminals. Ordering an Uber to your friends’ house puts both your and their location at risk, and making online purchases exposes your credit card information?—?a mistake that can lead to serious financial fraud. Having your social security number leaked over the internet could lead to a torrent of trouble at the hands of an unscrupulous identity thief.
The stakes get even higher, however, when connectivity is used to amplify the services in whose hands we put our lives. Modern cars, airplanes, ships, and even medical devices have added internet connections to expand the range of services they offer. Using your phone to adjust your pacemaker is incredibly convenient, but the damage a hacker could cause with control of it is literally life threatening. Without the appropriate protective measures in place, all digital information can be turned into a weapon to threaten people.
Modern vehicles are connected to the internet wirelessly, and also use a number of additional radio interfaces: Bluetooth, remote unlocking and starting of vehicles, wireless tire pressure monitoring systems, wired iOS and Android interfaces…
The electronics in your vehicle keep record of the places you visited?—?if equipped with navigation, they remember your driving style, how you accelerate and how often you break hard. If you use the Bluetooth connection to make phone calls in your car the electronics may keep a list if your contacts, or the history of your calls and messages.
Connectivity-enabled transportation has numerous hurdles barring its way to success. Unique, unprecedented situations involving multiple vehicles, their passengers, and their data need to be secured from start to finish to ensure the safety of the people depending on connected vehicles”.

Even worse, in addition to one’s own actions, this “digital self” is also indirectly threatened by confidential information in various companies’ databases. Are these companies doing the right thing to protect us and themselves? Antoine Matthey-Doret, from Dathena, provides an answer:
“Imagine a very messy office open to everyone, files and folders lying everywhere: this is what most data centers look like today. Even if the office is locked with a key, you want to make sure that no matter what happens, the confidential information does not get stolen. As we know that no system is perfect, there is a need to proactively protect the confidential information. However, people do not know what is sensitive or not or even what the company has to protect. And doing this manually would be a nightmare. Automated classification allows exhaustive and granular inventory of all these documents by business category and by level of confidentiality to protect and monitor information.
The 7 reasons for data classification are the following:
· Handle your data appropriately: data classification enables organizations and employees to regain control over their data knowing where each type of record is stored.
· Measure your protection: identifying which files are being protected, as well as how and why. This way you are able to proactively detect potential security lacks.
· Prevent insider threats: data classification combined with identity and access management technology helps by only allowing the right people to access to documents on a need-to-know basis.
· Prevent outsider threats: data classification combined with data loss prevention technologies help to prevent unauthorized third parties from seeing information they shouldn’t.
· Find data quickly: data classification enables efficient data retrieval, which has become a key point for organizations with new regulations such as GDPR. (The C-Suite UK, 2017)
GDPR stands for General Data Protection Regulation. It’s a new European regulation which revolutionizes data privacy addressing the way data should be stored, transferred and collected online. Its aim is to give European residents greater control and visibility over their personal data, strengthening and unifying data protection.
Cybersecurity technologies can help organizations navigate within their petabytes of data and regain control over it: this is Dathena’s mission. Leveraging the power of Artificial Intelligence, Dathena automatically classifies data, identifies personal information, detects security anomalies and protects sensitive information”.

Businesses really need be aware of cybersecurity solutions in order to prevent any risks of data leaks or others attacks that might happen against them. Eric Houdet, from Quarkslab, gives us some advice about what we can easily put in place at work:
“The primary focus of INFOSEC (Information Security) is the balanced protection of the confidentiality, integrity and availability of data while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a multi-step risk management process that identifies assets, threat sources, vulnerabilities, potential impacts, and possible controls, followed by assessment of the effectiveness of the risk management plan.
To standardize this discipline, academics and professionals collaborate and seek to set basic guidance, policies, and industry standards on password, antivirus software, firewall, encryption software, legal liability and user/administrator training standards. This standardization may be further driven by a wide variety of laws and regulations that affect how data is accessed, processed, stored, and transferred. However, the implementation of any standards and guidance within an entity may have limited effect if a culture of continuous improvement isn’t adopted.
But attackers target data, not the infrastructure which needs to be constantly:
· monitored with usually a security operations center (SOC) where a centralized unit deals with security issues on an organizational and technical level;
· tested with regular authorized simulated attack on a computer system, performed to evaluate the security of the system. The test is performed to identify both weaknesses, also referred to as vulnerabilities;
· and updated.
Therefore, Quarkslab focuses on data security, with 3 products: IRMA, Ivy, and Epona. These products, coming along our service and training offers, help organizations take security decisions at the right time based on relevant information.
At Quarkslab, we see security as a means of fulfillment. With security you can look ahead, with confidence. We give meaning to security, seen not as a self-serving abstraction but as a concrete means for accomplishing ambitions”.
Cybersecurity is a critical technology for the digital age: without it, there can be no trust, no services, no transactions, no digitization, no growth, no citizenship. As a world leading company in this industry and others, Thales is proud to be working with the crème de la crème of cybersecurity start-ups worldwide, and to provide the best secured solutions that make the world go round, whatever it takes. Learn more about the Cyber@StationF programme and the start-ups on their website.

Cybersecurity is a hot subject area on university campuses nationwide. In particular, schools in the state of Michigan are refining curricula to produce professionals capable of defending against the increasingly complex nature of cybercrime and intrusion in both government and industry.
That’s why Trillium’s latest stop on the Hack Across America tour was the University of Detroit-Mercy (UDM). The school is a Department of Homeland Security (DHS) and National Security Agency (NSA) designated Center of Academic Excellence in Cyber Defense (CAE-CD). Over forty students attended the engagement on UDM’s campus on November 8th, 2019.
During the presentations given by Trillium’s sales engineer and cloud engineer on the need for securing the data generated by connected vehicles, UDM students were engaged and asked many questions. They exhibited a strong grasp of encryption technologies, familiarity with CAN bus networks, and deep interest in work placements at Trillium’s Ann Arbor office location. The two-hour discussion which followed the presentations was marked by intense curiosity about Trillium’s multi-layered cybersecurity solution, its online car hacking simulation called PassGO, and how a trusted mobility platform and data management services can be deployed to make connected vehicles safe.
To find out where the next CAE-CD stop of Hack Across America will be, follow Trillium Secure on LinkedIn, or visit trilliumsecure.com.
Email
Phone
Address
SecureGO
SecureFAST
SecureLINK
SecureSKYE
Services & Tools
